Finally after a year of on/off studying, I passed the CompTIA Security+ exam. For a quick overview, before I started studying, I used TryHackMe, took most of Jeremy’s IT CCNA […]
Category: Uncategorized
Frigate NVR – Local Machine Learning Video Processing (with people tracking)
Well – Since Kubernetes was a bust – I figured I should start trying to do some of the video analysis of my network locally. I got a Google […]
First Kubernetes Cluster
I wanted to try out Kubernetes for a bunch of reasons, but mostly to get a redundant solution for Frigate and Home Assistant. In the end, I realized Kubernetes is […]
Buying a used Fortigate 60-E
For better or worse, I bought myself a Fortigate 60-E to mess around with – a ton of folks I work with use them; these devices are everywhere. So I […]
Descent into deCONZ – A Zigbee Smarthome
I have been playing around with a variety of smart home devices, and have had much success with Home Assistant running on my Raspberry Pi 4, using a Raspbee […]
Install Mongodb on Ubuntu Server 22.04
Little set of instructions to install Mongodb on Ubuntu Server 22.04 sudo apt install dirmngr gnupg apt-transport-https ca-certificates software-properties-common echo “deb http://security.ubuntu.com/ubuntu impish-security main” | sudo tee /etc/apt/sources.list.d/impish-security.list Go to […]
Proxmox Update Pt 2 – The HBA Strikes Back
One goal of updating to Proxmox was to be able to run TrueNAS Core as a VM, which would then have my NAS in a ZFS Pool. To do this, […]
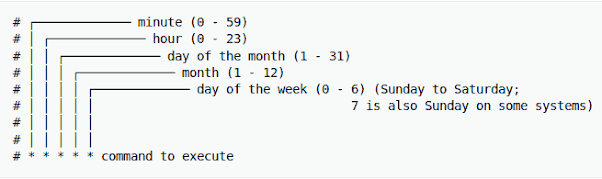
Setting Up ZFS Scrubbing with Cron Jobs
I have a ZFS pool as my main Network Attached Storage (NAS) as well as it’s backup. To make sure the data doesn’t get corrupted, it’s important to verify […]
What is MSS Clamping and how it could effect YOUR VPNs
TL;DR: If you’re experiencing slow traffic on your VPN, try lowering the MSS size. This could prevent your router from segmenting packets and lead to a more efficient connection. […]
Proxmox Server Upgrades
For the past few months, I’ve been playing with TrueNAS Scale, and for a few reasons I’ll be leaving it behind for Proxmox. My goal is to build a server […]
PiHole for DNS Blocking on pfSense
Pi-hole is a Linux network-level advertisement and Internet tracker blocking application, which acts as a DNS sinkhole and optionally a DHCP server, intended for use on a private network. […]
Network Logging with Greylog on RaspberryPi
After successfully getting a Zabbix server working on Raspberry Pi, I was looking for something that could aggregate logs. Zabbix had a great UI, but i wanted something where I […]
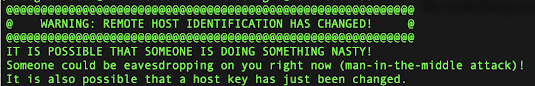
Clearing SSH Host Keys on Mac
Have you seen this? To fix it – open a terminal. Run: cd ~/.ssh Then: open . This will open a folder. Open the known_hosts file and delete the entries […]
Slapping Mr Beast 100 Million times – Exploiting Local Storage
This was reported to Mr. Beast’s team on August 15, 2022 immediately after this was posted. Also – Big Thank You to CaliD – couldn’t have done it without ya. […]
Creating Evil – Testing Network Defenses
If you have a homelab and want to test out your defenses, check out a few of these projects to help you “Create Evil” to find with Security Onion or […]
Subdomain Enumeration
Was just messing around with subdomain enumeration and wanted to give a quick overview of a few tools I find useful: hakrawler, gau, theHarvester, sublist3r, gobuster, and recon-ng. For the […]
Notes on NIST Risk Management Framework
This is a brief summary about the basics of the NIST 800-37 Rev 2 – Risk Management Framework (RMF). Link to the course I took is at the bottom of […]